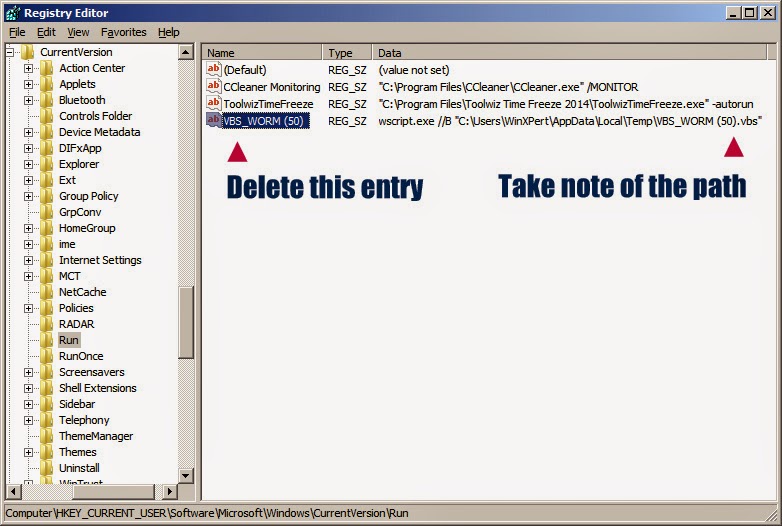
Terminating a malicious process. More than one way to skin a cat.
Your options are numerous. We can start with what Windows already has provided us. Task Manager and Taskkill.
Using Task Manager
You may have already know how to lauch Task Manager. Ctrl+Alt+Del, Ctrl-Shift+Esc, Right click on Taskbar and Start Task Manager, Launch it via Run [Win+R], etc- Launch Task Manager
- Go to the Processes tab
- Hightlight the process you want to terminate
- Click on the End Process tab at the lower right corner
- or Right Click on the process and Select either End Process or End Process Tree
Using Taskkill
The syntax for TASKKILL for terminating a process isTASKKILL /F /IM ProcessName.exe
Lets's do a quick demo. Launch Notepad and run the following
TASKKILL /F /IM Notepad.exe
You can run this command at the CMD Prompt or with the Run [Win+R]
Using 3rd Party Utilities
No need for too much explanations here, I'll just provide my screenshots. These are better alternatives to Task ManagerIf you find this tutorial useful, please comment, share or email me. You can also make a donation to my PayPal account to help me continue my work. Thank you.
arnaldo.austria@gmail.com
Pinoy Tech RAMBO
To GOD be the glory!
All content ("Information") contained in this report is the copyrighted work of WinXPert: Virus and Malware Removal.
The Information is provided on an "as is" basis. WinXPert disclaims all warranties, whether express or implied, to the maximum extent permitted by law, including the implied warranties that the Information is merchantable, of satisfactory quality, accurate, fit for a particular purpose or need, or non-infringing, unless such implied warranties are legally incapable of exclusion. Further, WinXPert does not warrant or make any representations regarding the use or the results of the use of the Information in terms of their correctness, accuracy, reliability, or otherwise.
Copyright © 2014-2015 WinXPert. All rights reserved. All other trademarks are the sole property of their respective owners.








.vbs.bmp)