Removable USB/thumb
drives use the Autorun feature to load files when the drives are plugged
into the USB port. Malware exploits the Autorun feature to spread from
thumb drive to PC. Disable the autorun feature to prevent malware from
spreading.
1. The easiest and most effective means to truly disable autorun can be done via this simple autorun registry hack:
REGEDIT4
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\IniFileMapping\Autorun.inf]
@="@SYS:DoesNotExist"
2. To use this method, Open Notepad and copy/paste the following into a text file:
REGEDIT4
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\IniFileMapping\Autorun.inf]
@="@SYS:DoesNotExist"
Save
the file as something.reg. (You have to be sure to change the "Save
File as Type" to "All Files" before saving, or Windows will try to save
it as a .txt even if you typed in .reg.
3. Locate the
file you just saved and double-click the file to run it. You will
receive a prompt asking if you want to add the data to the registry.
Click yes to allow the modification.
4. The above
method nulls any request for autorun.inf and works on XP Home or Pro, as
well as Windows Vista. Credit for this tip goes to Nick Brown.
If
you opt to disable autorun using any other method, you will first need
to install an autorun patch from Microsoft that allegedly resolves
issues that cause autorun to run even after it's been disabled (using
methods other than the above recommended method).
5.
XP Pro users who have installed the appropriate Microsoft patch for your
system and wish to disable autorun using a method other than described
above, follow steps 3 through 8 only. XP Home users begin at step 9.
6. Windows XP Pro users: Click
Start and then click
Run. Type
gpedit.msc and click OK. The Group Policy window will open. In the left pane, double-click
Administrative Templates
7. In the right pane, double-click
System, scroll down the list and double-click
Turn Off Autoplay
8. In the
Turn Off Autoplay Properties window, select
Enabled. From the dropdown next to
Turn Off Autoplay on, select
All drives and then click
OK. Exit
Group Policy by selecting
File, then choosing
Exit from the menu.
9. XP Home users will need to make the changes by editing the registry directly. To begin, click
Start and then click
Run
10. Type
regedit and click
OK. The Registry Editor window will open.
11. In the left pane, navigate to:
HKEY_CURRENT_USER
Software
Microsoft
Windows
CurrentVersion
Policies
Explorer.
12. With
Explorer highlighted, in the right-pane right click the value
NoDriveTypeAutoRun and select
Modify from the drop down menu. The base value will be set to Hexadecimal. If not, select Hexadecimal.
13. Type
95 and click
OK.
Note
that this will stop Autorun on removable/USB drives, but still allow it
on CD ROM drives. If you want to disable autorun on both, substitute b5
for the 95. (Thanks to Ian L. of Manitoba for the tip).
14. Exit
Registry Editor by selecting
File, then choosing
Exit from the menu.
15. You will now need to reboot your computer for the changes to take effect.
Source:
http://antivirus.about.com/od/securitytips/ht/autorun.htm
How to Disable Autorun in Vista
A
bug in Microsoft Vista executes programs in the Autorun.inf file when
the Autorun feature has been disabled via the NoDriveTypeAutoRun
registry value. If you've set the value NoDriveTypeAutoRun in the
Windows Vista registry, delete the value and follow the steps below to
really disable autorun in Vista.
Note: the steps below involved editing the System Registry.
Here's How:
1. The easiest and most effective means to truly disable autorun can be done via this simple autorun registry hack:
REGEDIT4
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\IniFileMapping\Autorun.inf]
@="@SYS:DoesNotExist"
2.
The above method nulls any request for autorun.inf and works on XP
Home or Pro, as well as Windows Vista. Credit for this tip goes to Nick
Brown.
If you opt to disable autorun using any other
method, you will first need to install an autorun patch from Microsoft
that allegedly resolves issues that cause autorun to run even after it's
been disabled (using methods other than the above recommended method).
3. The following steps apply to Windows Vista users only. See:
How to Disable Autorun (Posted below)
4. Open the Registry Editor (regedit.exe) and browse to the following key:
HKLM\SYSTEM\CurrentControlSet\Services\Cdrom
5. In the right pane, right-click Autorun and select Modify.
6. Enter 0 for the Value data. Click OK, then exit the Registry Editor
7. Click Start, type autoplay and press enter. If prompted by User Access Control (UAC), click Continue.
8. Remove the check from 'Use AutoPlay for all media and devices'
You may also wish to change each individual item to 'Take no action'
9. Click Save and the Autoplay window will close.
10.
The following steps involve using the Group Policy Editor (gpedit.msc).
This feature is not available in Windows Vista Home or Windows Vista
Home Premium editions.
11. Click Start, type gpedit.msc
and press enter. If prompted by User Access Control (UAC), click
Continue. The Group Policy Object Editor will open.
12. In the left pane under Computer Configuration, double click Administrative Templates, then double click Windows Components.
13. In the right pane, double click AutoPlay Policies and select (double click) 'Default Behavior for AutoRun'.
14.
In the Default Behavior for Autorun Properties dialog, select Enabled.
In the Default Autorun Behavior field, select Do not execute any autorun
commands
15. Click Apply, then click OK and close the Group Policy Object Editor.
Source:
http://antivirus.about.com/od/securitytips/ht/vista_autorun.htm
How To Autorun Worms: How to Remove Autorun Malware
Autorun
worms spread from USB/thumb drives as well as fixed and mapped drives.
Autorun worms typically drop or download additional malware, usually
backdoors and password stealers. For a description of how Autorun
malware works, see the Autorun FAQs. To remove an Autorn worm, follow
the steps below.
Here's How:
1. Before attempting removal of an autorun worm, you must first disable Autorun. See:
How to Disable Autorun or
How to Disable Autorun in Vista posted below.
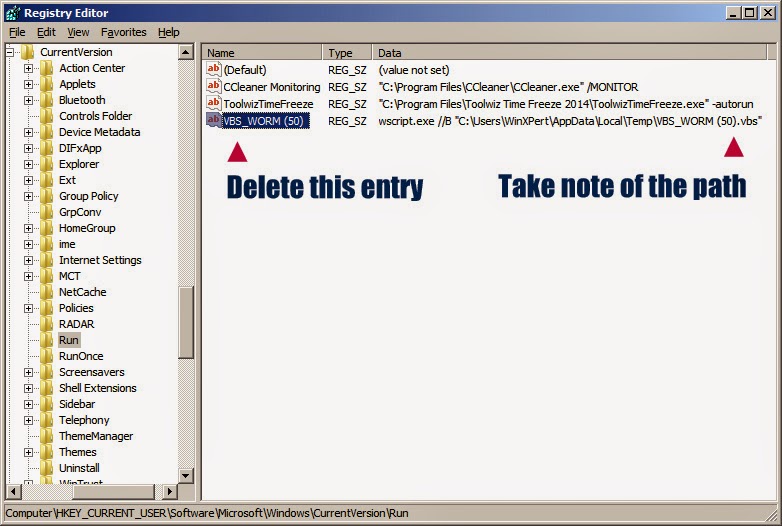
2.
After you have disabled autorun, search the root of all drives
(including all USB/thumb drives) for the presence of an autorun.inf
file. When you have located the autorun.inf file, open it using a text
editor such as Notepad and look for any lines that begin with Label="
and "shellexecute=". Note the name of the file designated by these
lines.
3. Close the autorun.inf file and delete it from
the drive. Now locate the file that was designated in Step 2 and delete
that file as well.
4. Repeat these steps for all local, mapped, and removable drives.
5.
Note that if an autorun worm is discovered, you should anticipate other
infections have occurred and also that your antivirus/firewall/security
software may have been disabled and/or tampered with. Ensure the
antivirus is working properly by using an Eicar test file.
6.
If you are unable to delete the malware files, or they reappear after
deleting, use a bootable antivirus rescue CD to access the drive without
allowing the malware to load first. You should then be able to delete
the target files.
Source:
http://antivirus.about.com/od/virusdescriptions/ht/autorunworms.htm



































.vbs.bmp)