II. Registry Tweaks
Blocking program execution
This technique is similar to what gpedit.msc would do when you don't allow an application from executing. We will be using two registry scripts to accomplish this. One is for blocking and another for unblocking.Copy/paste the following and save it as Block.reg. Just like in How to block or prevent malware from running Part 1, we'll be using wscript.exe as our example.
Windows Registry Editor Version 5.00
; Block an application
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer]
"DisallowRun"=dword:00000001
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\DisallowRun]
"1"="wscript.exe"
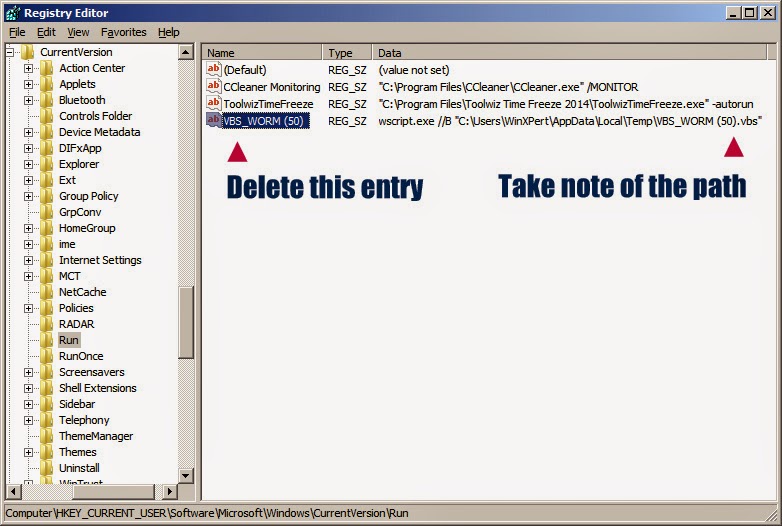
 |
| Running a VBS File with restrictions |
When you're done with scanning and your system is already clean from infections, you can unblock wscript.exe by using the next registry script. Save the following as Unblock.reg.
Windows Registry Editor Version 5.00
; Unblock an application
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer]
"DisallowRun"=-
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\DisallowRun]
"1"=-
Note that this technique is not limited to VBS worms. I used this method for removing malwares like Daprosy worms, or any unknown trojan that can't be deleted easily because it's locked by a running process. Sometimes, only gpedit.msc, taskman, regedit and cmd are all you need to remove low to medium malware threats.
Making Notepad the default file handler for VBS files
Another way to prevent VBS worms from running is to use Notepad instead of WScript as VBE and VBS files default file handler. This way the worm would open in Notepad instead of executing making it easier to remove.Copy/paste the following and save it as "Open VBE VBS with Notepad.reg"
Windows Registry Editor Version 5.00
;Open VBE/VBS file with Notepad by WinXPert
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\VBEFile\Shell\Open\Command]
@=hex(2):22,00,25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,6f,00,74,\
00,25,00,5c,00,53,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,00,4e,00,\
6f,00,74,00,65,00,70,00,61,00,64,00,2e,00,65,00,78,00,65,00,22,00,20,00,25,\
00,31,00,00,00
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\VBSFile\Shell\Open\Command]
@=hex(2):22,00,25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,6f,00,74,\
00,25,00,5c,00,53,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,00,4e,00,\
6f,00,74,00,65,00,70,00,61,00,64,00,2e,00,65,00,78,00,65,00,22,00,20,00,25,\
00,31,00,00,00
 |
| Opening a VBS File with Open VBE VBS with Notepad.reg merged to registry. |
And here is the companion script to revert VBE/VBS handling back to it's default settings. Save this one as "Open VBE VBS with WScript (Default).reg"
Windows Registry Editor Version 5.00
;Open VBE/VBS file with WScript.exe (default)
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\VBEFile\Shell\Open\Command]
@=hex(2):22,00,25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,6f,00,74,\
00,25,00,5c,00,53,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,00,57,00,\
53,00,63,00,72,00,69,00,70,00,74,00,2e,00,65,00,78,00,65,00,22,00,20,00,22,\
00,25,00,31,00,22,00,20,00,25,00,2a,00,00,00
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\VBSFile\Shell\Open\Command]
@=hex(2):22,00,25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,6f,00,74,\
00,25,00,5c,00,53,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,00,57,00,\
53,00,63,00,72,00,69,00,70,00,74,00,2e,00,65,00,78,00,65,00,22,00,20,00,22,\
00,25,00,31,00,22,00,20,00,25,00,2a,00,00,00
 |
| Running a VBS File with default file handler |
To be continued...
Please visit my blog on manual malware removal
All my tutorials are FREE. If you find this tutorial useful, please comment or share. You can also help fund my continued work by making a donation. Thank you and GOD bless!
To GOD be the glory!
All content ("Information") contained in this report is the copyrighted work of WinXPert: Virus and Malware Removal.
The Information is provided on an "as is" basis. WinXPert disclaims all warranties, whether express or implied, to the maximum extent permitted by law, including the implied warranties that the Information is merchantable, of satisfactory quality, accurate, fit for a particular purpose or need, or non-infringing, unless such implied warranties are legally incapable of exclusion. Further, WinXPert does not warrant or make any representations regarding the use or the results of the use of the Information in terms of their correctness, accuracy, reliability, or otherwise.
Copyright © 2015 WinXPert. All rights reserved. All other trademarks are the sole property of their respective owners.
















.vbs.bmp)























.png)